Your cart is currently empty!
Snake Keylogger Lifetime Shared License
Unleash the Power of Snake Keylogger
Lifetime Shared License – One Payment, Forever Access to Premium Intelligence Gathering
- Lifetime Access
- Shared Cost Benefits
- Full Feature Access
- Value Proposition
$50
One-Time Payment
Lifetime
License Duration
$500+
Value Saved
Ready to Deploy?
Get permanent access to one of the most sophisticated keyloggers available.
Secure Lifetime License
Why Choose Snake Keylogger?
Snake Keylogger, also recognized in the cybersecurity landscape as 404 Keylogger or KrakenKeylogger, stands as a formidable .NET-based Trojan meticulously engineered to target Windows endpoints and extract a wealth of sensitive information.
Why Our Lifetime License is the Ultimate Deal?
Our exclusive lifetime shared license for the original Snake Keylogger presents an unparalleled opportunity: one $50 payment grants you permanent access to premium surveillance capabilities without recurring fees or subscription headaches.
Compared to traditional subscription models that cost $25-500 per month, our lifetime license saves you $500+ in the first year alone. The shared license model makes this powerful tool accessible at a fraction of exclusive license costs while maintaining all premium features.
Masterful Features Designed for Maximum Intelligence Gathering
| Feature | Description | Key Targets/Data Types | Evasion Techniques |
|---|---|---|---|
| Comprehensive Keystroke Logging | Meticulously records every key pressed by the victim, including usernames, passwords, messages, and financial details. | All keyboard input, including secure fields; special function keys; system commands. | Low-level API hooks (e.g., SetWindowsHookEx). |
| Advanced Credential Theft | Extracts saved credentials from web browsers, email clients, FTP programs, and other applications. | Browsers (Chrome, Firefox, Edge); email clients; FTP; WiFi passwords; cookies; autofill data. | Leverages hooks/APIs to access browser password storage; parses files/registry entries. |
| Stealthy Screenshot Capture | Takes periodic or triggered screenshots of the victim’s desktop, providing visual context to logged data. | Entire screen or specific application windows; graphical information; 2FA codes (if displayed). | Operates without alerting the victim; images compressed before exfiltration. |
| Clipboard Data Monitoring | Monitors and captures data copied to the system clipboard, such as passwords or cryptocurrency addresses. | Text, images, files copied to clipboard; passwords from managers; crypto addresses. | Periodically checks clipboard or registers for update notifications. |
| Robust Data Exfiltration | Transmits stolen data to the attacker via multiple channels, including SMTP, FTP, and Telegram bots. | SMTP, FTP, Telegram, Pastebin; data often compressed and encrypted before transfer. | Uses encrypted channels (e.g., SMTP over SSL/TLS); multiple methods for resilience. |
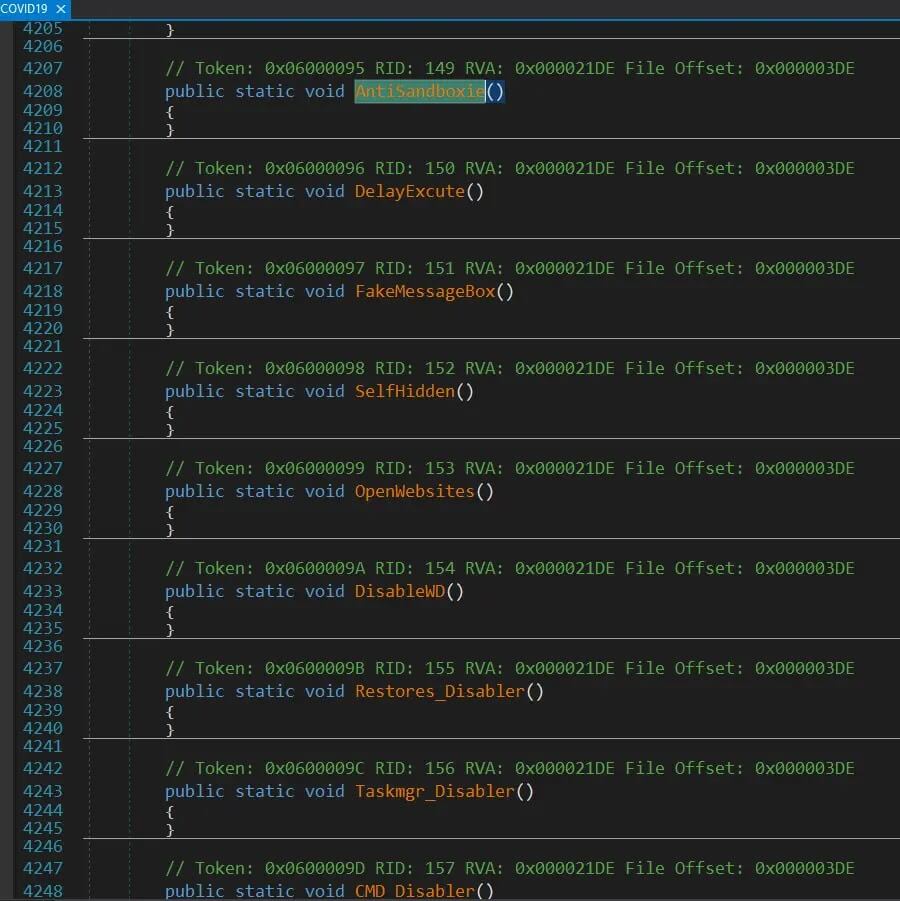
| Evasion and Persistence | Employs techniques like obfuscation, process hollowing, and startup scripts to operate undetected and survive reboots. | Obfuscation (AutoIt); process hollowing (e.g., RegSvcs.exe); startup scripts (VBS); registry keys; Defender exclusions. | Deletes initial dropper files; adds to Windows Defender exclusion list. |
Comprehensive Keystroke Logging
At the core of Snake Keylogger’s capabilities is its sophisticated keystroke logging functionality, designed to meticulously record every key pressed by the victim on their keyboard. This fundamental feature enables the attacker to capture a vast array of sensitive information including usernames, passwords, personal messages, and financial details.
The keylogger employs Windows API functions, specifically SetWindowsHookEx, to intercept keystrokes at a low level, ensuring comprehensive coverage of all user input.
Advanced Credential Theft
Beyond basic keystroke logging, Snake Keylogger is equipped with advanced mechanisms specifically designed to steal saved credentials from a wide array of applications, most notably popular web browsers including Google Chrome, Mozilla Firefox, and Microsoft Edge.
This capability significantly enhances its effectiveness as an information stealer, as many users rely on their browsers to store passwords for numerous online accounts.
Stealthy Screenshot Capture
A critical feature that enhances the intelligence-gathering capabilities of Snake Keylogger is its ability to capture screenshots of the victim’s desktop. This functionality provides a visual context to the data obtained through keystroke logging and credential theft, allowing the attacker to literally “see what the victim sees” on their screen.
The screenshot feature can be configured to capture the entire screen or specific application windows at regular intervals or triggered by specific events.
Clipboard Data Monitoring
Recognizing that users often rely on copy-paste operations to manage complex passwords or transfer sensitive information, Snake Keylogger incorporates a feature to monitor and capture data from the system clipboard. This is particularly effective for stealing passwords that users copy from a password manager or a document rather than typing them manually.
The clipboard monitoring function works by periodically checking the contents of the clipboard or by registering for clipboard update notifications from the operating system.
Robust Data Exfiltration
Once Snake Keylogger has successfully collected a wealth of sensitive information through its various logging and theft mechanisms, it needs a reliable way to transmit this data back to the attacker. The malware is known for its relatively unusual and versatile methods of data exfiltration, which include sending stolen data via SMTP (Simple Mail Transfer Protocol) email servers, FTP (File Transfer Protocol), and even through messaging applications like Telegram bots.
The use of encrypted channels for data transmission, such as SMTP over SSL/TLS or Telegram’s inherent encryption, helps to evade detection by network monitoring tools.
Evasion and Persistence
A hallmark of Snake Keylogger’s sophistication is its advanced evasion and persistence mechanisms, designed to ensure it remains undetected and operational on the victim’s system for extended periods. The malware employs a variety of techniques including obfuscation tools, such as AutoIt scripting, to hide its malicious payload within seemingly benign files.
Furthermore, Snake Keylogger utilizes process hollowing, a technique where it injects its malicious code into trusted Windows processes (e.g., RegSvcs.exe).
Technical Prowess of Snake Keylogger
.NET-Based Architecture
Snake Keylogger is predominantly developed using the .NET framework, a software framework developed by Microsoft that runs primarily on Microsoft Windows. This choice of architecture provides several advantages for malware development, including the relative ease of programming complex functionalities and access to a rich set of libraries.
The .NET architecture allows for sophisticated features like advanced credential theft and data exfiltration mechanisms seen in Snake Keylogger.
Anti-Analysis Techniques
Snake Keylogger incorporates a range of anti-analysis and anti-detection techniques to evade security software and hinder reverse engineering efforts. One primary method is code obfuscation, which involves transforming the malware’s code into a more complex and difficult-to-understand form without altering its functionality.
The use of AutoIt scripting in some variants is another layer of obfuscation, as AutoIt can compile scripts into executable files that may appear benign or be harder for static analysis tools to dissect.
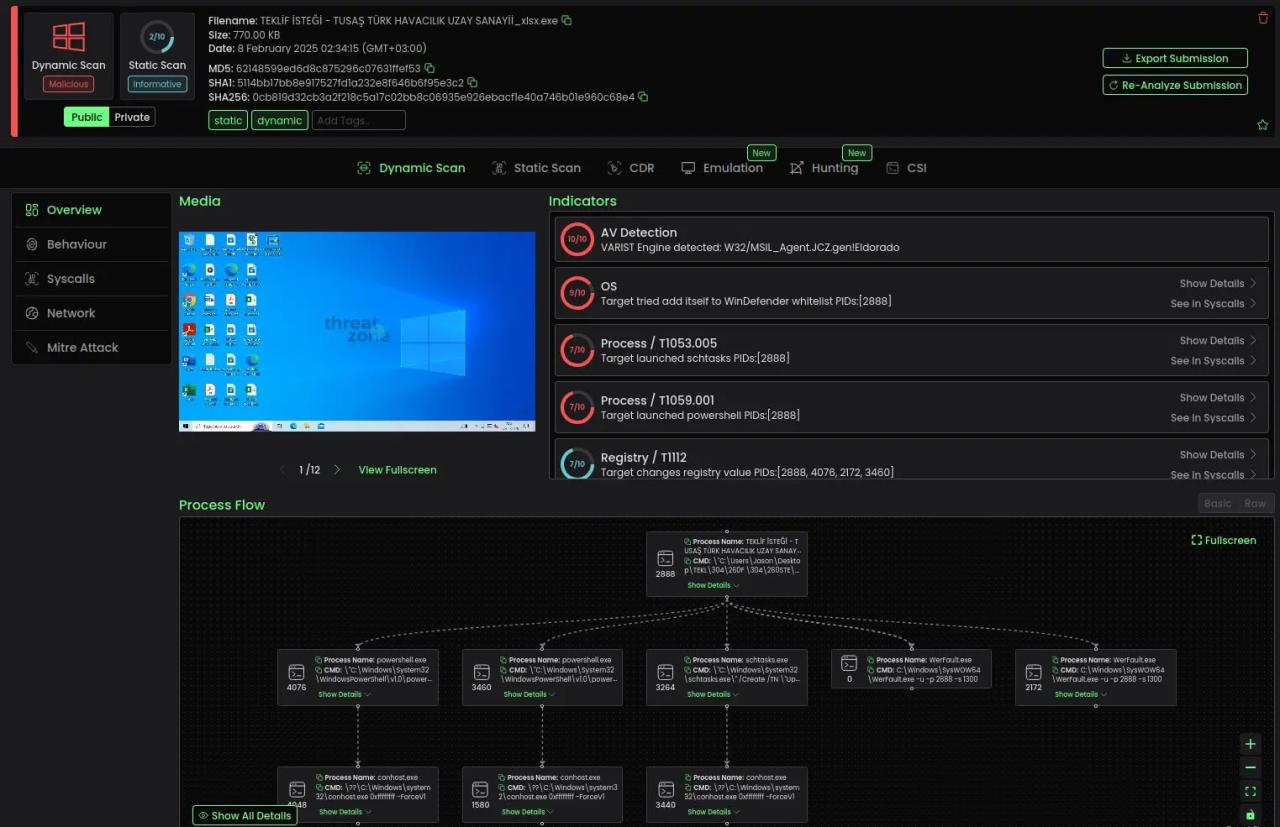
Process Hollowing and Code Injection
Snake Keylogger frequently employs process hollowing, a sophisticated code injection technique, to execute its malicious payload while evading detection. This method involves creating a new instance of a legitimate Windows process, such as RegSvcs.exe (a .NET utility), in a suspended state.
The malware then “hollows out” the memory space of this legitimate process by unmapping its original code and data sections, injects its own malicious code, and resumes execution. This technique allows the keylogger to operate with a degree of stealth, bypassing security measures that might detect a standalone malicious executable.
Process Hollowing Execution Flow:
- Create Legitimate Process (e.g., RegSvcs.exe) in Suspended State
- Hollow Out Process Memory (Unmap Original Code/Data)
- Inject Malicious Code (Snake Keylogger Payload)
- Resume Process Execution (Now Running Malicious Code)
- Operates Stealthily Under Legitimate Process Context
Pricing and Licensing: Lifetime Access for $50
The Ultimate Value: Lifetime License
We’re revolutionizing access to premium malware capabilities with our exclusive lifetime license for Snake Keylogger. For a single payment of $50, you get permanent access to all features – no renewals, no subscriptions, just unlimited operational capability.
- $50 One-Time Payment
- Lifetime Access Duration
- Shared Cost Advantages
Why Lifetime Beats Subscriptions:
- Save $500+ annually compared to $25-500/month subscription models
- No recurring payments – pay once, use forever
- Shared license model provides premium access at budget pricing
- All future updates included at no extra cost
- Cost-effective for long-term operations with zero ongoing expenses
Why Our Snake Keylogger Lifetime License is Unbeatable
Permanent Access
Your $50 investment grants lifetime access to all current and future features of Snake Keylogger. No renewals, no expiration – just permanent operational capability.
Massive Savings
Compared to standard $25-500/month subscriptions, our lifetime license pays for itself in 1-2 months and saves you thousands long-term.
Continuous Updates
Receive all future updates and enhancements at no additional cost. Our developers continuously improve evasion techniques and compatibility.
Shared Benefits
The shared license model makes premium capabilities accessible at budget pricing without compromising on features or performance.
Proven Effectiveness
Snake Keylogger has a documented history of effectiveness with over 280 million blocked infection attempts globally.
Immediate Deployment
Get instant access after payment. Ideal for both short-term operations and long-term intelligence gathering needs.
Act Now – Limited Lifetime Licenses Available!
Exclusive Offer
This lifetime license deal is a limited-time opportunity. We can’t guarantee how long we’ll be able to maintain this unprecedented pricing model.
Only 47 licenses remaining at this price point before all revert to subscription models.
Risk-Free Investment
With our 30-day money-back guarantee, you can test Snake Keylogger’s capabilities risk-free. If it doesn’t meet your operational needs, we’ll refund your payment.
Your satisfaction is guaranteed – we stand behind our product’s capabilities.


Leave a Reply